Office 365 Single Sign-On
Available on Enterprise and Professional plans
self-hosted deployments
Available in legacy Mattermost Enterprise Edition E20
Configuring Office 365 as a Single Sign-On (SSO) service
Follow these steps to configure Mattermost to use your Office 365 logon credentials and Azure Active Directory account as a Single Sign-on (SSO) service for team creation, account creation, and sign-in.
Note
The system must be using SSL as Microsoft only allows OAuth redirect URIs that are SSL-enabled.
Step 1: Register an application in Azure Portal
Log in to the Azure Portal with the account that relates to the Azure Active Directory tenant where you want to register the application. You can confirm the tenant in the top right corner of the portal.
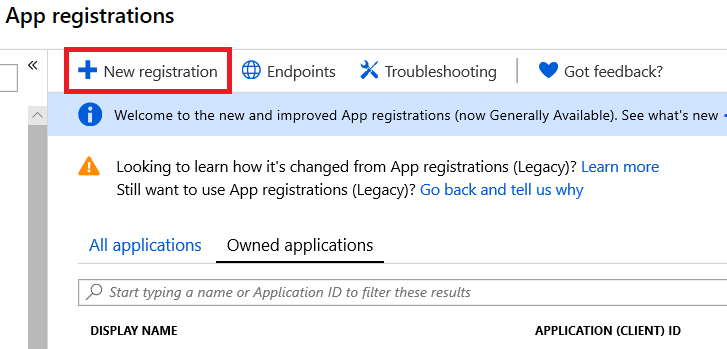
In the left-hand navigation pane, select the Azure Active Directory service, then select App registrations > New registration.
Give your new registration a Name.
Define which Supported account types can access the application. For example, if this is to be only accessed from your enterprise’s Azure AD accounts, then select Accounts in this organizational directory only.
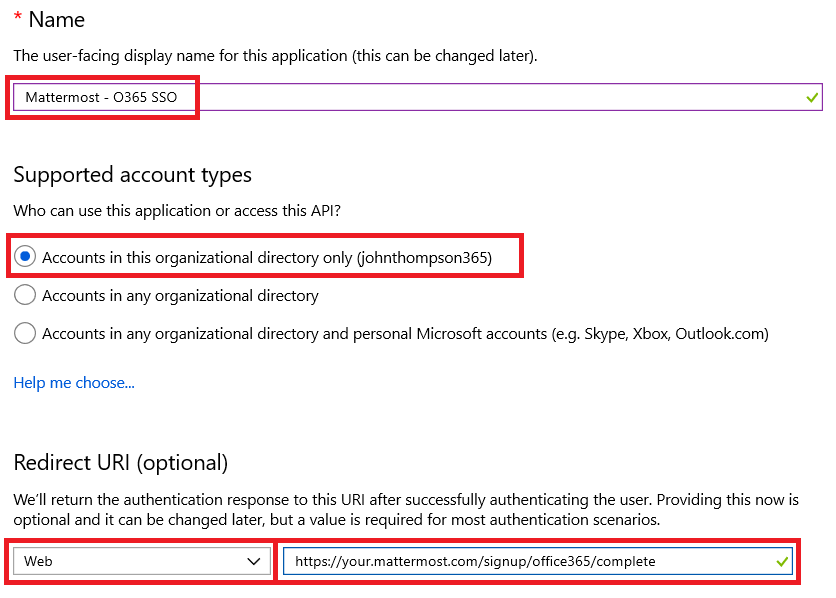
Define the Redirect URI as Web client, then input the URL with the host name that will be specific to your Mattermost service followed by
/signup/office365/complete. An example below is:https://your.mattermost.com/signup/office365/complete
Once the App Registration has been created, you can configure it further. See the standard Azure AD documentation for reference.
Step 2: Generate a new client secret in Azure Portal
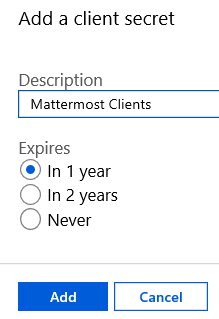
In the Azure Portal, select Certificates and Secrets from the menu, then select the button to generate a New Client secret.
Provide a description, define the expiry for the token, then select Add.
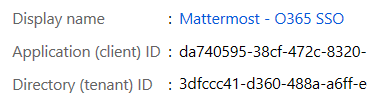
In Azure Portal, select Overview from the menu, then copy and paste both the Application (client) ID and the Directory (tenant) ID to a temporary location. You will enter these values as an Application ID and as part of an Auth Endpoint and Token Endpoint URL in the Mattermost System Console.
Step 3: Configure Mattermost for Office 365 SSO
Log in to Mattermost, then go to System Console > Authentication > OpenID Connect.
Select Office 365 as the service provider.
Paste the Directory (tenant) ID from the Azure Portal as the Directory (tenant) ID in Mattermost.
The Discovery Endpoint for OpenID Connect with Office 365 is prepopulated with
https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration.Paste the Application (client) ID from the Azure Portal as the Client ID in Mattermost.
Paste the client secret value from the Azure Portal as the Client Secret in Mattermost.
Select Save.
Note
When Mattermost is configured to use OpenID Connect or OAuth 2.0 for user authentication, the following user attribute changes can’t be made through the Mattermost API: first name, last name, or username. OpenID Connect or OAuth 2.0 must be the authoritative source for these user attributes.
Note about Microsoft Active Directory Tenants
A Microsoft Active Directory (AD) tenant is a dedicated instance of Azure Active Directory (Azure AD) that you own and would have received when signing up for a Microsoft cloud service, such as Azure or Office 365. Tenants are commonly used by organizations who want to store information about their users, such as passwords, user profile data, and permissions. You can learn more about getting an Azure AD tenant here.
To allow your Azure AD users to log in to Mattermost using Office 365 SSO, you must register Mattermost in the Microsoft Azure AD tenant that contains the users’ information. The registration can be done from the Microsoft Azure portal. The steps to register the Mattermost account in the tenant should be similar to those provided above, and you can find more information about integrating apps with Azure AD here.
If you don’t register Mattermost in the Microsoft Azure AD tenant your organization uses, Office 365 SSO will likely fail for your users.
Note
If you do not use Azure Active Directory, you may register Mattermost with your Office 365 or Azure account (a personal, work, or school account), then set up Office 365 SSO with Mattermost using the steps provided above.
Configure Mattermost config.json for Office 365 SSO
Available on Enterprise and Professional plans
self-hosted deployments
Instead of using the System Console, you can add the Office 365 settings directly to the config.json file on your Mattermost server.
Open
config.jsonas root in a text editor. It’s usually in/opt/mattermost/configbut it might be elsewhere on your system.Locate the
Office365Settingssection, then add or update the following information:
"Enable": false,
"Secret": "i.hddd6Pu3--5dg~cRddddqOrBdd1a",
"Id": "28ddd714-1f2f-4f9c-9486-90b8dddd27",
"Scope": "profile openid email",
"AuthEndpoint": "",
"TokenEndpoint": "",
"UserApiEndpoint": "",
"DiscoveryEndpoint": "https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration",
"DirectoryId": "common"
}
Save your changes, then restart your Mattermost server. After the server restarts, users must change their login method before they can log in with Office 365.
Frequently Asked Questions
How can I use LDAP attributes or Groups with OpenID?
At this time, LDAP data isn’t compatible with OpenID. If you currently rely on LDAP to manage your users’ teams, channels, groups, or attributes, you won’t be able to do this automatically with users who have logged in with OpenID. If you need LDAP synced to each user, we suggest using SAML or LDAP as the login provider. Some OpenID providers can use SAML instead, like Keycloak.
































