Authentication configuration settings
Available on all plans
Cloud and self-hosted deployments
Mattermost supports up to four distinct, concurrent methods of Authentication:
An OpenID provider
A SAML provider
An LDAP instance (e.g., Active Directory, OpenLDAP)
Email and Password
Both self-hosted and Cloud admins can access the following configuration settings in System Console > Authentication. Self-hosted admins can also edit the config.json file as described in the following tables.
Signup
Available on all plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > Signup.
Enable account creation
|
|
Restrict account creation to specified email domains
This setting limits the email address domains that can be used to create a new account or team. You must set Require Email Verification to String input of a comma-separated list of domains, i.e. |
|
Enable open server
|
|
Enable email invitations
|
|
Note: Cloud admins can’t modify this configuration setting. |
|
Invalidate pending email invites
This button invalidates email invitations that have not been accepted (by default, invitations expire after 48 hours). This option has no |
|
Available on all plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > Email.
Enable account creation with email
|
|
Note: Cloud admins can’t modify this configuration setting. |
|
Require email verification
|
|
Enable sign-in with email
|
|
Enable sign-in with username
|
|
Password
Available on all plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > Password.
Minimum password length
This feature was moved to Team Edition in Mattermost v5.0, released June 16th, 2018. Prior to v5.0, this feature is available in legacy Enterprise Edition E10 and E20.
This setting determines the minimum number of characters in passwords. It must be a whole number greater than or equal to 5 and less than or equal to 64. Numerical input. Default is 5. |
|
Password requirements
This feature was moved to Team Edition in Mattermost v5.0, released June 16th, 2018. Prior to v5.0, this feature is available in legacy Enterprise Edition E10 and E20.
This setting controls password character requirements. By checking the corresponding box, passwords must contain:
The error message previewed in the System Console will appear if the user attempts to set an invalid password. The default for all boxes is unchecked. The default for all settings in |
|
Maximum login attempts
This setting determines the number of failed sign-in attempts a user can make before being locked out and required to go through a password reset by email. Numerical input. Default is 10. |
|
MFA
Available on all plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > MFA.
We recommend deploying Mattermost within your own private network, and using VPN clients for mobile access, so that Mattermost is secured with your existing protocols. If you choose to run Mattermost outside your private network, bypassing your existing security protocols, we recommend adding a multi-factor authentication service specifically for accessing Mattermost.
Enable multi-factor authentication
|
|
Enforce multi-factor authentication
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E10 and E20
|
|
Note: If your system has users who authenticate with methods other than AD/LDAP and email, MFA must be enforced with the authentication provider outside of Mattermost. |
|
AD/LDAP
Available on Enterprise and Professional plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > AD/LDAP.
Enable sign-in with AD/LDAP
Available in legacy Enterprise Edition E10 and E20
|
|
Enable synchronization with AD/LDAP
Available in legacy Enterprise Edition E10 and E20
|
|
Note: Synchronization with AD/LDAP settings in the System Console can be used to determine the connectivity and availability of arbitrary hosts. System admins concerned about this can use custom admin roles to limit access to modifying these settings. See the system admin roles documentation for details. |
|
Login field name
Available in legacy Enterprise Edition E10 and E20
This setting will display placeholder text in the login field of the sign-in page. This text can remind users to sign-in with their AD/LDAP credentials. String input. Default is |
|
AD/LDAP server
Available in legacy Enterprise Edition E10 and E20
This is the domain name or IP address of the AD/LDAP server. String input. |
|
Note: Synchronization with AD/LDAP settings in the System Console can be used to determine the connectivity and availability of arbitrary hosts. System admins concerned about this can use custom admin roles to limit access to modifying these settings. See the system admin roles documentation for details. |
|
AD/LDAP port
Available in legacy Enterprise Edition E10 and E20
This is the port Mattermost uses to connect to the AD/LDAP server. Numerical input. Default is 389. |
|
Connection security
Available in legacy Enterprise Edition E10 and E20
This setting controls the type of security Mattermost uses to connect to the AD/LDAP server, with these options:
|
|
Skip certificate verification
Available in legacy Enterprise Edition E10 and E20
|
|
Private key
Available in legacy Enterprise Edition E10 and E20
Use this setting to upload the private key file from your LDAP authentication provider, if TLS client certificates are the primary authentication mechanism. String input. |
|
Public certificate
Available in legacy Enterprise Edition E10 and E20
Use this setting to upload the public TLS certificate from your LDAP authentication provider, if TLS client certificates are the primary authentication mechanism. String input. |
|
Bind username
Available in legacy Enterprise Edition E10 and E20
This is the username for the account Mattermost utilizes to perform an AD/LDAP search. This should be an account specific to Mattermost. Limit the permissions of the account to read-only access to the portion of the AD/LDAP tree specified in the Base DN setting. When using Active Directory, Bind Username should specify domain in String input. |
|
Note: This field is required. Anonymous bind is not currently supported. |
|
Bind password
Available in legacy Enterprise Edition E10 and E20
This is the password for the username given in the Bind Username setting. String input. |
|
Base DN
Available in legacy Enterprise Edition E10 and E20
This is the Base Distinguished Name of the location in the AD/LDAP tree where Mattermost will start searching for users. String input. |
|
User filter
Available in legacy Enterprise Edition E10 and E20
This setting accepts a general syntax AD/LDAP filter that is applied when searching for user objects. Only the users selected by the query can access Mattermost. For example, to filter out disabled users, the filter is: To filter by group membership, determine the String input. |
|
Note: This filter uses the permissions of the Bind Username account to execute the search. This account should be specific to Mattermost and have read-only access to the portion of the AD/LDAP tree specified in the Base DN field. |
|
Group filter
Note
Available only on Enterprise plans
Available in legacy Enterprise Edition E20
This setting accepts a general syntax AD/LDAP filter that is applied when searching for group objects. Only the groups selected by the query can access Mattermost. String input. Default is |
|
Note: This filter is only used when AD/LDAP Group Sync is enabled. See AD/LDAP Group Sync for more information. |
|
Enable admin filter
Available in legacy Enterprise Edition E20
|
|
Note: If this setting is |
|
Admin filter
Available in legacy Enterprise Edition E20
This setting accepts an AD/LDAP filter that designates the selected users as System Admins. Users are promoted to this role on their next sign-in or on the next scheduled AD/LDAP sync. If the Admin Filter is removed, users who are currently logged in retain their Admin role until their next sign-in. String input. |
|
Guest filter
Available in legacy Enterprise Edition E20
This setting accepts an AD/LDAP filter to apply when searching for external users with Guest Access to Mattermost. Only users selected by the query can access Mattermost as Guests. See Guest Accounts for more information. String input. |
|
ID attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that is serves as a unique user identifier in Mattermost. The attribute should have a unique value that does not change, such as String input. |
|
Note: If a user’s ID Attribute changes, a new Mattermost account is created that is not associated with the previous account. If you need to change this field after users have signed-in, use the mattermost ldap idmigrate CLI tool. |
|
Login ID attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that is used for signing-in to Mattermost. This is normally the same as the Username Attribute. If your team uses String input. |
|
Username attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that populates the username field in Mattermost. This attribute identifies users in the UI. For example, if a Username Attribute is set to This is normally the same as the Login ID Attribute, but it can be mapped to a different attribute. String input. |
|
Email attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in AD/LDAP server that populates the email address field in Mattermost. Email notifications are sent to this address. The address may be seen by other Mattermost users depending on privacy settings. String input. |
|
First name attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that populates the first name field in Mattermost. When set, users cannot edit their first name. When not set, users can edit their first name in their profile settings. String input. |
|
Last name attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that populates the last name field in Mattermost. When set, users cannot edit their last name. When not set, users can edit their last name as part of their profile settings. String input. |
|
Nickname attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that populates the nickname field in Mattermost. When set, users cannot edit their nickname. When not set, users can edit their nickname as part of their profile settings. String input. |
|
Position attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that populates the position field in Mattermost. When set, users cannot edit their position. When not set, users can edit their position as part of their profile settings. String input. |
|
Profile picture attribute
Available in legacy Enterprise Edition E10 and E20
This is the attribute in the AD/LDAP server that syncs and locks the profile picture in Mattermost. The image is updated when users sign-in, not when Mattermost syncs with the AD/LDAP server. The image is not updated if the Mattermost image already matches the AD/LDAP image. String input. |
|
Group display name attribute
Note
Available only on Enterprise plans
Available in legacy Enterprise Edition E20
This is the AD/LDAP Group Display name attribute that populates the Mattermost group name field. String input. |
|
Note: This attribute is only used when AD/LDAP Group Sync is enabled and it is required. See the AD/LDAP Group Sync documentation for more information. |
|
Group ID attribute
Note
Available only on Enterprise plans
Available in legacy Enterprise Edition E20
This is an AD/LDAP Group ID attribute that sets a unique identifier for groups. This should be a value that does not change, such as String input. |
|
Note: This attribute is only used when AD/LDAP Group Sync is enabled and it is required. See the AD/LDAP Group Sync documentation for more information. |
|
Synchronization interval (minutes)
Available in legacy Enterprise Edition E10 and E20
This value determines how often Mattermost syncs with the AD/LDAP server by setting the number of minutes between each sync. Syncing with the AD/LDAP server will update Mattermost accounts to match any changes made to AD/LDAP attributes. Disabled AD/LDAP accounts become inactive users in Mattermost, and any active sessions are revoked. Use the AD/LDAP Synchronize Now button to immediately revoke a session after disabling an AD/LDAP account. Numerical input. Default is 60. |
|
Note: LDAP syncs require a large number of database read queries. Monitor database load and adjust the sync interval to minimize performance degradation. |
|
Maximum page size
Available in legacy Enterprise Edition E10 and E20
This setting paginates the results of AD/LDAP server queries. Use this setting if your AD/LDAP server has a page size limit. The recommended setting is 1500. This is the default AD/LDAP A page size of 0 disables pagination of results. Numerical input. Default is 0. |
|
Query timeout (seconds)
Available in legacy Enterprise Edition E10 and E20
This setting determines the timeout period, in seconds, for AD/LDAP queries. Increase this value to avoid timeout errors when querying a slow server. Numerical input. Default is 60. |
|
AD/LDAP test
Available in legacy Enterprise Edition E10 and E20
Use this button to test the connection to the AD/LDAP server. If the test succeeds, a confirmation message is displayed. If the test fails, an error message is displayed. |
|
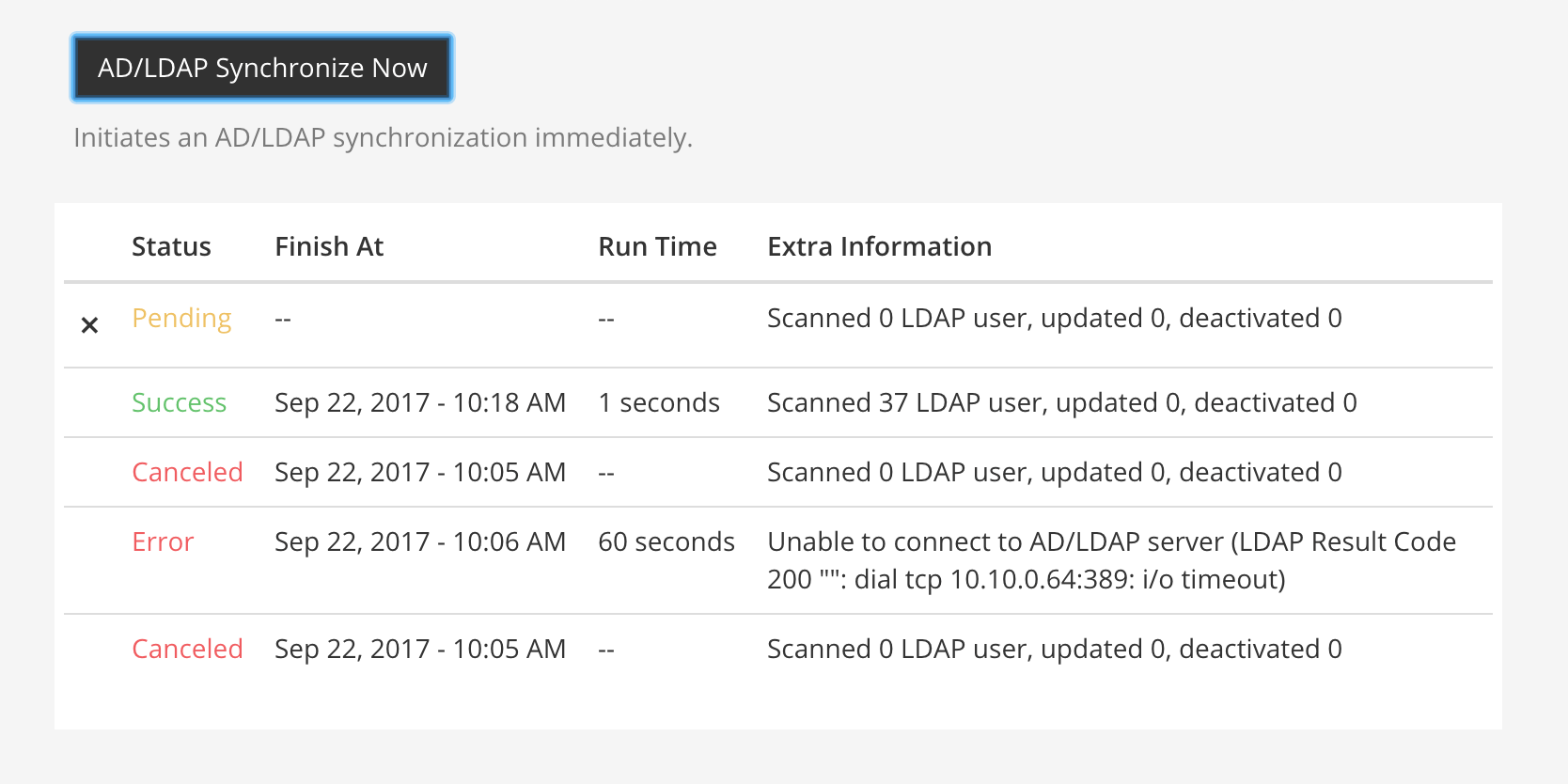
AD/LDAP synchronize now
Available in legacy Enterprise Edition E10 and E20
Use this button to immediately sync with the AD/LDAP server. The status of the sync is displayed in the table underneath the button (see the figure below). Following a manual sync, the next sync will occur after the time set in the Synchronization Interval. |
|
Note: If a sync is |
|
SAML 2.0
Available on Enterprise and Professional plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > SAML 2.0.
Note
In line with Microsoft ADFS guidance we recommend configuring intranet forms-based authentication for devices that do not support WIA.
Enable login with SAML
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
|
|
Enable synchronizing SAML accounts with AD/LDAP
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
See AD/LDAP Setup and Advanced User Management to learn more. |
|
Ignore guest users when synchronizing with AD/LDAP
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
For more information, see AD/LDAP Setup and Advanced User Management. |
|
Override SAML bind data with AD/LDAP information
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
For more information, see AD/LDAP Setup and Advanced User Management. |
|
|
|
Identity provider metadata URL
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting is the URL from which Mattermost requests setup metadata from the provider. String input. |
|
SAML SSO URL
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting is the URL where Mattermost sends a SAML request to start the login sequence. String input. |
|
Identity provider issuer URL
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting is the issuer URL for the Identity Provider for SAML requests. String input. |
|
Identity provider public certificate
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
The public authentication certificate issued by your Identity Provider. String input. |
|
Verify signature
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
|
|
Service provider login URL
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
Enter the URL of your Mattermost server, followed by Use HTTP or HTTPS depending on the configuration of the server. This setting is also known as the Assertion Consumer Service URL. |
|
Service provider identifier
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting is the unique identifier for the Service Provider, which in most cases is the same as the Service Provider Login URL. In ADFS, this must match the Relying Party Identifier. String input. |
|
Enable encryption
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
|
|
Service provider private key
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting stores the private key used to decrypt SAML Assertions from the Identity Provider. String input. |
|
Service provider public certificate
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting stores the certificate file used to sign a SAML request to the Identity Provider for a SAML login when Mattermost is initiating the login as the Service Provider. String input. |
|
Sign request
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
|
|
Signature algorithm
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting determines the signature algorithm used to sign the SAML request. Options are: String input. |
|
Canonical algorithm
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting determines the canonicalization algorithm. With these options:
String input. |
|
Email attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting determines the attribute from the SAML Assertion that populates the user email address field in Mattermost. Notifications are sent to this email address. This email address may be visible to other users, depending on how the System Admin has set-up user privacy. String input. |
|
Username attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
This setting determines the SAML Assertion attribute that populates the username field in the Mattermost UI. This attribute identifies users in the UI. For example, if a username is set to String input. |
|
Id attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute used to bind users from SAML to users in Mattermost. String input. |
|
Guest attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute used to apply a Guest role to users in Mattermost. See the Guest Accounts documentation for more information. String input. |
|
Enable admin attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
|
|
Admin attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the attribute in the SAML Assertion for designating System Admins. Users are automatically promoted to this role when logging in to Mattermost. If the Admin attribute is removed, users that are logged in retain Admin status. The role is revoked only when users log out. String input. |
|
First name attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute that populates the first name of users in Mattermost. String input. |
|
Last name attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute that populates the last name of users in Mattermost. String input. |
|
Nickname attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute that populates the nickname of users in Mattermost. String input. |
|
Position attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute that populates the position (job title or role at company) of users in Mattermost. String input. |
|
Preferred language attribute
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) This setting determines the SAML Assertion attribute that populates the language preference of users in Mattermost. String input. |
|
Login button text
Note
Available only on Enterprise and Professional plans
Available in legacy Enterprise Edition E20
(Optional) The text that appears in the login button on the sign-in page. String input. Default is SAML. |
|
OAuth 2.0
Available on Enterprise and Professional plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > OAuth 2.0. Settings for GitLab OAuth authentication can also be accessed under Authentication > GitLab in self-hosted deployments.
Use these settings to configure OAuth 2.0 for account creation and login.
Select OAuth 2.0 service provider
Available in legacy Enterprise Edition E20
Use this setting to enable OAuth and specify the service provider, with these options:
|
|
GitLab OAuth 2.0 settings
Available on all plans
Cloud and self-hosted deployments
Note
For Enterprise subscriptions, GitLab settings can be found under OAuth 2.0
Enable OAuth 2.0 authentication with GitLab
|
|
GitLab OAuth 2.0 Application ID
This setting holds the OAuth Application ID from GitLab. Generate the ID by these steps:
String input. |
|
Note: GitLab provides the Application Secret Key along with the the ID. |
|
GitLab OAuth 2.0 Application secret key
This setting holds the OAuth Application Secret Key from GitLab. The key is generated at the same time as the Application ID (see GitLab OAuth 2.0 Application ID). Enter the key provided by GitLab in the Mattermost System Console field, String input. |
|
GitLab OAuth 2.0 site URL
This setting holds the URL of your GitLab instance, e.g. |
|
GitLab OAuth 2.0 User API endpoint
This setting holds the URL of your GitLab User API endpoint, e.g. Enter the URL in the Mattermost System Console field, String input. |
|
GitLab OAuth 2.0 Auth endpoint
This setting holds the URL of your GitLab Auth endpoint, e.g. Enter the URL in the Mattermost System Console field, String input. |
|
GitLab OAuth 2.0 Token endpoint
This setting holds the URL of your GitLab OAuth Token endpoint, e.g. Enter the URL in the Mattermost System Console field, String input. |
|
Google OAuth 2.0 settings
Available on Enterprise and Professional plans
self-hosted deployments
Enable OAuth 2.0 authentication with Google
|
|
Google OAuth 2.0 Client ID
Available in legacy Enterprise Edition E20
This setting stores the OAuth Client ID from Google. Generate the ID by going to the Credentials section of the Google Cloud Platform APIs & Services menu and selecting Create Credentials > OAuth client ID. See Google Single Sign-On for instructions that can be used to implement Google OAuth or OpenID authentication. String input. |
|
Google OAuth 2.0 Client secret
Available in legacy Enterprise Edition E20
This setting stores the OAuth Client Secret from Google. The Secret is generated at the same time as the Client ID. String input. |
|
Google OAuth 2.0 User API endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
Google OAuth 2.0 Auth endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
Google OAuth 2.0 Token endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
Office 365 OAuth 2.0 settings
Available on Enterprise and Professional plans
self-hosted deployments
Note
In line with Microsoft ADFS guidance we recommend configuring intranet forms-based authentication for devices that do not support WIA.
Enable OAuth 2.0 Authentication with Office 365
|
|
Note: See the Office 365 Single Sign-On documentation for details. |
|
Office 365 OAuth 2.0 Application ID
Available in legacy Enterprise Edition E20
This setting holds the Application ID generated when configuring Office 365 as a Single Sign-On service through the Microsoft Azure Portal. String input. |
|
Note: See the Office 365 Single Sign-On documentation for details. |
|
Office 365 OAuth 2.0 Application secret password
Available in legacy Enterprise Edition E20
This setting holds the Application Secret Password generated when configuring Office 365 as a Single Sign-On service through the Microsoft Azure Portal. String input. |
|
Note: See the Office 365 Single Sign-On documentation for details. |
|
Office 365 OAuth 2.0 Directory (tenant) ID
Available in legacy Enterprise Edition E20
This setting holds the Directory (tenant) ID set for Mattermost through the Azure Portal. String input. |
|
Note: See the Office 365 Single Sign-On documentation for details. |
|
Office 365 OAuth 2.0 User API endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
Office 365 OAuth 2.0 Auth endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
Office 365 OAuth 2.0 Token endpoint
Available in legacy Enterprise Edition E20
We recommend String input. |
|
OpenID Connect
Available on all plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > OpenID Connect.
Select OpenID Connect service provider
Available in legacy Enterprise Edition E20
Choose whether OpenID Connect can be used for account creation and login. Options include:
Do not allow login via an OpenID provider
GitLab (available in all plans; see GitLab Settings for details)
Google Apps (Available in Mattermost Enterprise and Professional; see Google Settings for details)
Office 365 (Available in Mattermost Enterprise and Professional; see Office 365 Settings for details)
OpenID Connect (Other) (Available in Mattermost Enterprise and Professional; see OpenID Connect Settings for more detail)
This feature’s setting does not appear in config.json.
GitLab settings
Available on Enterprise and Professional plans
self-hosted deployments
GitLab site URL
Available in legacy Enterprise Edition E10 and E20. Not available in Cloud Free.
Specify the URL of your GitLab instance (example https://example.com:3000). If your GitLab instance is not set up with SSL, start the URL with http:// instead of https://.
Discovery endpoint
Available in legacy Enterprise Edition E10 and E20 Not available in Cloud Free
Obtain this value by registering Mattermost as an application in your service provider account. Should be in the format https://myopenid.provider.com/{my_company}/.well-known/openid-configuration where the value of {my_company} is replaced with your organization.
Google Settings
Available on Enterprise and Professional plans
self-hosted deployments
Enable authentication with Google by selecting Google Apps from System Console > Authentication > OpenID Connect > Select service provider.
True: Allow team creation and account signup using Google OpenID Connect. To configure, input the Client ID, Client Secret, and DiscoveryEndpoint credentials. See the documentation for more detail.
False: Google OpenID Connect cannot be used for team creation or account signup.
This feature’s |
Discovery endpoint
Available in legacy Enterprise Edition E20
This value is prepopulated with https://accounts.google.com/.well-known/openid-configuration.
This feature’s |
Office 365 Settings
Available on Enterprise and Professional plans
self-hosted deployments
Note
In line with Microsoft ADFS guidance, we recommend configuring intranet forms-based authentication for devices that do not support WIA.
Enable authentication with Office 365 by selecting Office 365 from System Console > Authentication > OpenID Connect > Select service provider.
True: Allow team creation and account signup using Office 365 OpenID Connect. To configure, input the Application ID and Application Secret Password credentials. See the documentation for more detail.
False: Office 365 OpenID Connect cannot be used for team creation or account signup.
This feature’s |
Directory (tenant) ID
Available in legacy Enterprise Edition E20
This value is the ID of the application’s AAD directory.
Discovery endpoint
Available in legacy Enterprise Edition E20
This value is prepopulated with https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration.
OpenID Connect (other)
Available on Enterprise and Professional plans
Cloud and self-hosted deployments
Enable authentication with a service provider by selecting OpenID Connect (Other) from System Console > Authentication > OpenID Connect > Select service provider.
True: Allow team creation and account signup using OpenID Connect. To configure, input the Client ID, Client Secret, and DiscoveryEndpoint credentials. See the documentation for more detail.
False: OpenID Connect cannot be used for team creation or account signup.
This feature’s |
Button name
Available in legacy Enterprise Edition E20
Specify the text that displays on the OpenID login button.
This feature’s |
Button color
Specify the color of the OpenID login button for white labeling purposes. Use a hex code with a #-sign before the code, for example #145DBF.
This feature’s |
Discovery endpoint
Available in legacy Enterprise Edition E20
Obtain this value by registering Mattermost as an application in your service provider account. Should be in the format https://myopenid.provider.com/{my_company}/.well-known/openid-configuration where the value of {my_company} is replaced with your organization.
This feature’s |
Guest access
Available on Enterprise and Professional plans
Cloud and self-hosted deployments
Access the following configuration settings in the System Console by going to Authentication > Guest Access.
Enable guest access
Available in legacy Enterprise Edition E10 and E20
|
|
Note: See the Guest Accounts documentation for details. |
|
Whitelisted guest domains
Available in legacy Enterprise Edition E10 and E20
Use this setting to restrict the creation of guest accounts. When set, guest accounts require a verified email address from one of the listed domains. String input of one or more domains, separated by commas. |
|
Enforce multi-factor authentication
Available in legacy Enterprise Edition E10 and E20
|
|
Note: This setting defaults to false and cannot be changed if MFA isn’t enforced for non-guest users. |
|
































